

Secure Boot on PIC32CM LS60 Curiosity Pro Evaluation Kit
Download
Description
This application demonstrates the Secure Boot feature on the PIC32CM LS60 microcontroller (MCU). The application has two projects;
- A Secure Bootloader
- An Application
Following are the steps to demonstrate the secure boot:
Step 1: Secure Boot Configuration | Provisioning | Secure Booting
- The PIC32CM LS60 MCU is configured to run in secure boot mode with ATECC608B-based boot protection verification method and SHA-based NVM boot configuration (BOOTOPT=5).
- Program the Secure Bootloader code using Microchip’s Trust Platform Design Suite (TPDS).
- The successful running of the Secure Bootloader is indicated by turning the green LED0 ON.
- Receive the application image over UART from a PC by running a python script. The successful receiving of the application is indicated by toggling the red LED.
- Red LED1 starts toggling indicating secure and successful application booting.
Step 2: Impersonating Bootloader
- Generate a .hex file (say an impersonating bootloader) in MPLAB X IDE.
- Program the hex file using MPLAB X IDE (Ensure the bootloader is programmed at 0x00)
- Since the bootloader image in NVM is an impersonated one, it doesn’t have the digest matching the ATECC608 B-based authentication and integrity checks. The application fails to Boot. Both LED’s are OFF state.
Step 3: Restoring the Secure Bootloader and Validation
- Generate the Secure Bootloader .hex file in MPLAB X IDE.
- Use the Private/Public key used in Step 1 in TPDS and create the signed .hex file.
- Program the signed.hex file using the TPDS. The successful running of the Secure Bootloader is indicated by turning the green LED0 ON.
- Receive the application image over UART from a PC by running a python script. The successful receiving of the application is indicated by toggling the red LED.
- Since the Secure Bootloader is restored and the Secure Bootloader and application work as expected. Red LED1 starts toggling indicating secure and successful application booting.
Modules/Technology Used:
- Peripheral Modules
- Secure PORT Pins (All pins by default are secure)
- Secure I2C
- Secure RTC
- Secure EIC
- Secure USART
- System Modules
- Bootloader (UART)
Hardware Used:
Software/Tools Used:
This project has been verified to work with the following versions of software tools:
Refer Manifest file for Secure Bootloader project present in harmony-manifest-success.yml under the project folder firmware/secure_bootloader/Secure/firmware/src/config/pic32cm_ls60_cpro
- Note: Ignore NonSecure project(firmware/secure_bootloader/NonSecure/firmware/pic32cm_ls60_cpro_NonSecure.X) as it is a dummy project.
Refer Manifest file for the application project under Secure and Non Secure parts of the project present in harmony-manifest-success.yml under the folder firmware/test_app/{Secure or NonSecure}/firmware/src/config/pic32cm_ls60_cpro
- Refer the Release Notes to know the MPLAB X IDE and MCC Plugin version. Alternatively, Click Here.
- Trust Platform Design Suite V2
- Any Serial Terminal application like Tera Term terminal application.
- Python - v3 and above
Because Microchip regularly update tools, occasionally issue(s) could be discovered while using the newer versions of the tools. If the project doesn’t seem to work and version incompatibility is suspected, It is recommended to double-check and use the same versions that the project was tested with. To download original version of MPLAB Harmony v3 packages, refer to document How to Use the MPLAB Harmony v3 Project Manifest Feature
Hardware Setup:
-
The following diagram shows a detailed picture of the setup.
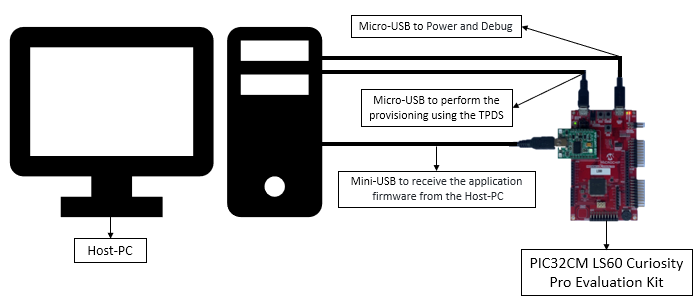
- The PIC32CM LS60 Curiosity Pro Evaluation Kit allows the Embedded Debugger (EDBG) to be used for debugging.
- Connect the Type-A male to Micro-B USB cable to Micro-B DEBUG USB port (J300) to power and debug the PIC32CM LS60 Curiosity Pro Evaluation Kit
- Connect the Type-A male to Micro-B USB cable to Target USB port (J200) to perform the provisioning using the TPDS tool on PIC32CM LS60 Curiosity Pro Evaluation Kit
-
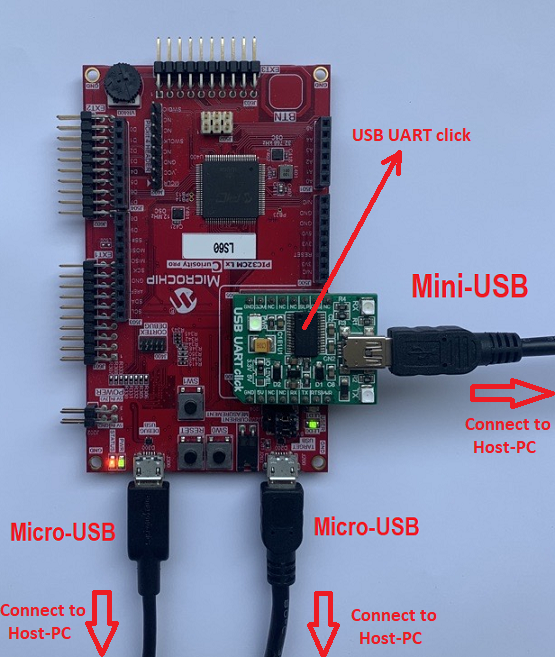
Mount MikroElektronika USB UART Click on microBus connector and connect the Type-A male to Mini-B USB cable to Mini-B USB-UART Cick onboard to receive the application firmware from the host.
Prerequisites:
- Install Trust Platform Design Suite V2 software.
- Generate Application’s Unified Binary. A Unified Binary is a single executable file generated by MPLAB X IDE using the Secure and NonSecure hex files. This can be used to program both Secure and Non-Secure regions together.
-
Note: The pre-built application hex and unified binary is kept in the hex folder. You can ignore the following steps if you have not modified the application project.
- Open and Build the Application’s NonSecure project in the MPLAB X IDE, i.e.,
reference_apps/apps/pic32cm_ls60_curiosity_pro/pic32cm_ls60_cpro_secure_boot/firmware/test_app/NonSecure/firmware/pic32cm_ls60_cpro_NonSecure.X - This will also build the mandatory Secure project.
-
- Steps to generate the PIC32CM LS60 User Row Configurations (Fuse Configurations) for Application project.
- The pre-generated application_user_configurations_out.txt configuration file will be used by the btl_host.py script to update the fuse configurations while programming the application.
- Note: The following steps shows how the application_user_configurations_out.txt file was generated based on the device and project configurations. You can ignore the following steps if you have not modified the project configurations.
- If modified then the input file application_user_configurations_in.txt needs to be generated based on the new device and project configuration and then passed to btl_dev_cfg_gen.py script file to generate the output file application_user_configurations_out.txt.
- The application_user_configurations_in.txt file consists of only the User Row Fuse configurations for the Non-Secure application project i.e., app_pic32cm_ls60_cpro_NonSecure project and it is generated by looking at the applications device and project configurations.
-
To know how this file is generated, open the above app_pic32cm_ls60_cpro_NonSecure project in MCC and check the Device & Project Configuration under System module. For example, the Memory Configurations of the application can be seen as below.
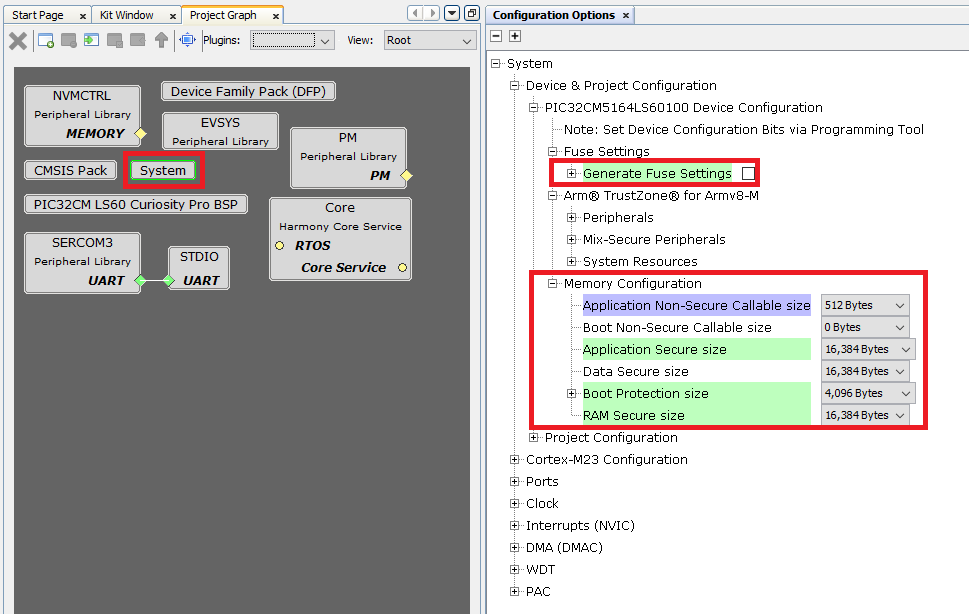
-
For more information on application_user_configurations_in.txt generation check the link Bootloader Device Input Configuration.
- Go to the scripts folder and execute the following command show help menu for the script.
-
python btl_dev_cfg_gen.py --help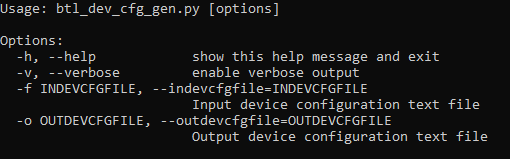
-
- The syntax for generating the device configuration output file is:
-
python btl_dev_cfg_gen.py -v -f <device_config_input_file.txt> -o <device_config_output_file.txt> -
To know more about btl_dev_cfg_gen.py - Refer Device Configuration Generation Script Help in Harmony UART Bootloader Library.
-
- Now, to generate the CRC for the fuse settings, execute the following command:
-
python btl_dev_cfg_gen.py -v -f application_user_configurations_in.txt -o application_user_configurations_out.txt
-
- The application_user_configurations_out.txt configuration file will be used later by the btl_host.py to update the fuse configurations while programming the application using Secure Bootloader.
Running the Demo:
- Perform Hardware Setup steps mentioned above, if not done already.
- Perform Prerequisites steps mentioned above, if not done already.
Step-1: Secure Boot Configuration | Provisioning | Secure Booting
- PIC32CM LS60 MCU is configured to run in secure boot mode with ATECC608B-based boot protection verification method and SHA-based NVM boot configuration (BOOTOPT=5).
- Open and Build the Secure Bootloader project in the MPLAB X IDE, i.e.,
reference_apps/apps/pic32cm_ls60_curiosity_pro/pic32cm_ls60_cpro_secure_boot/firmware/secure_bootloader/Secure/firmware/pic32cm_ls60_cpro_Secure.X
- Open and Build the Secure Bootloader project in the MPLAB X IDE, i.e.,
- Program the Secure Bootloader code using Mirochip’s Trust Platform Design Suite (TPDS).
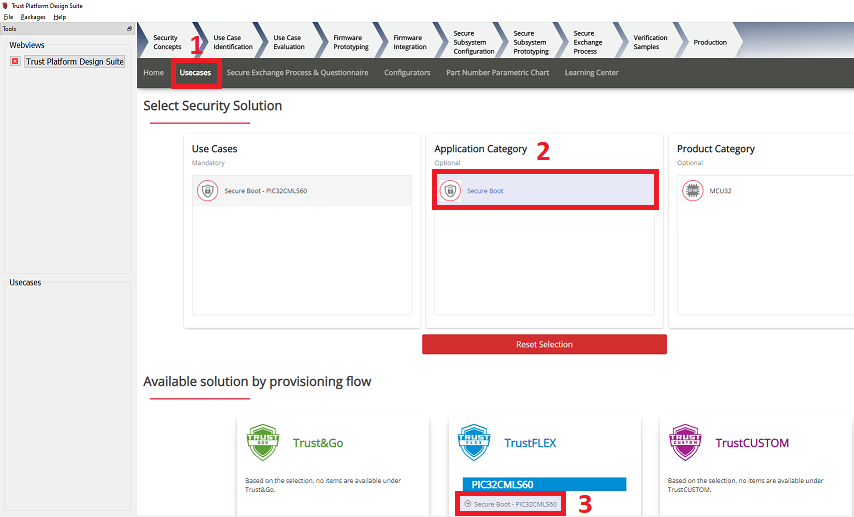
- Open the TPDS application and select the TrustFlex usecase, i.e., Secure Boot-PIC32CMLS60.
-
This usecase will sign an application hex file to support secure boot in combination with the ATECC608 embedded into the PIC32CM LS60. The application that is to be signed must be generated as per the current data sheet for secure boot.
-
-
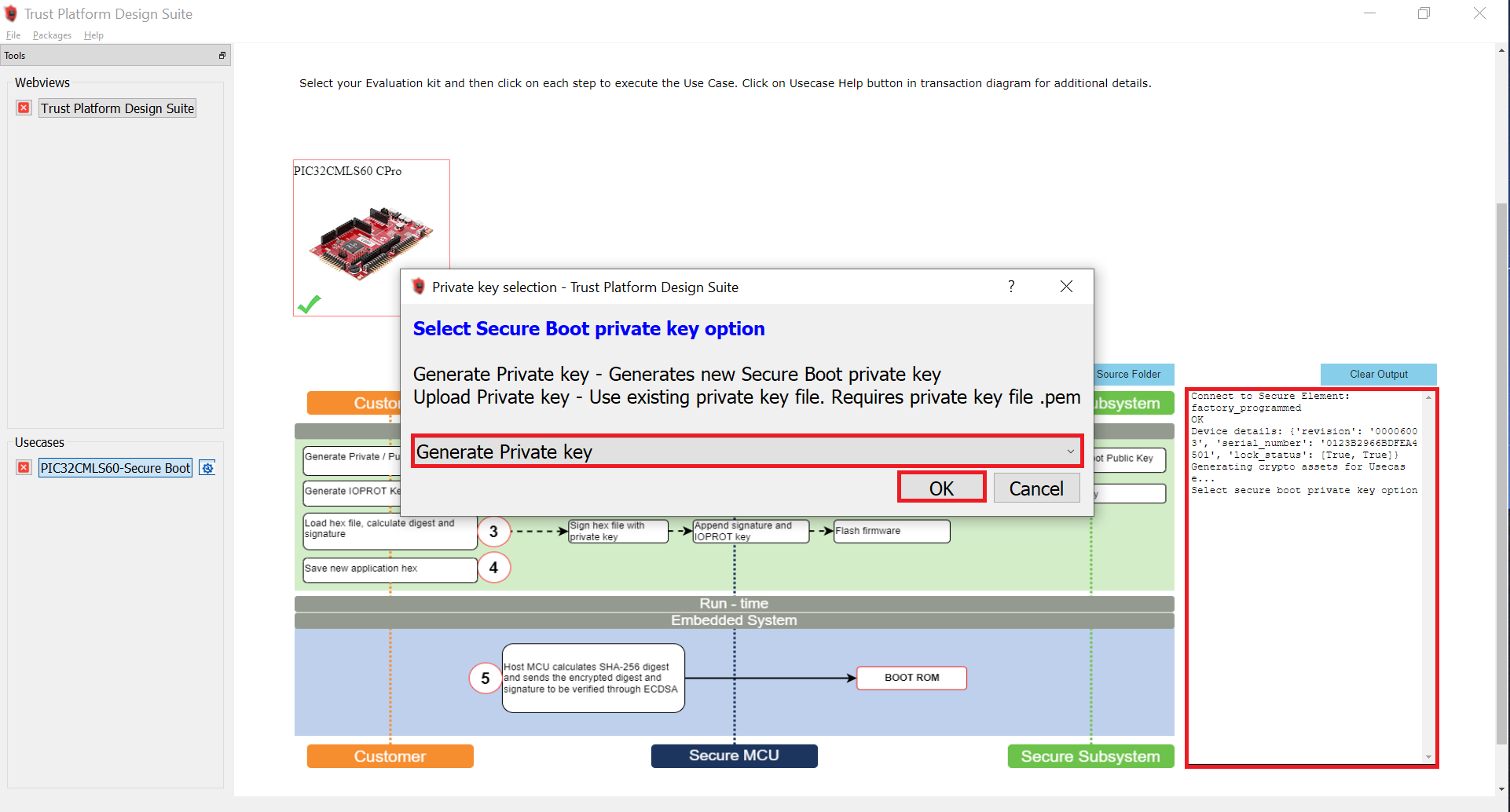
And click on Option 1 to Generate Private/Public key pair to perform the factory programming of default binary and wait for the response OK.
-
Press the reset button on the PIC32CM LS60 Curiosity Pro Evaluation Kit to sync with TPDS.
-
Again press Option 1 - Generate Private/Public key. In this step, the public key required to verify the SecureBoot is stored in Slot 15. This time a pop-up apears to Generate Private/Public key, as shown below.
-
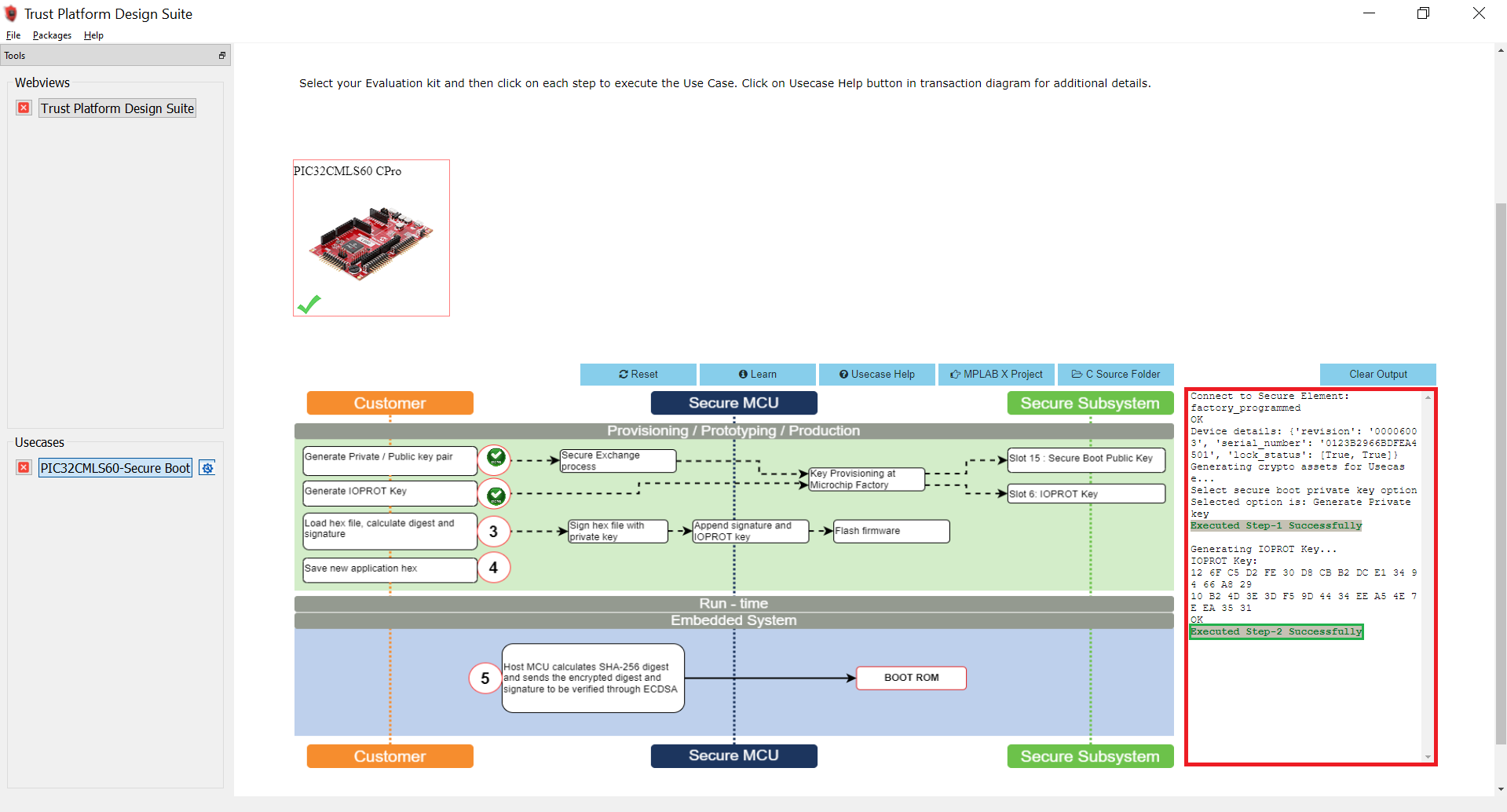
After successful execution of Option 1, a green tick mark appears in the Option 1 as shown below and check the log window for message “Executed Step-1 Successfully”.
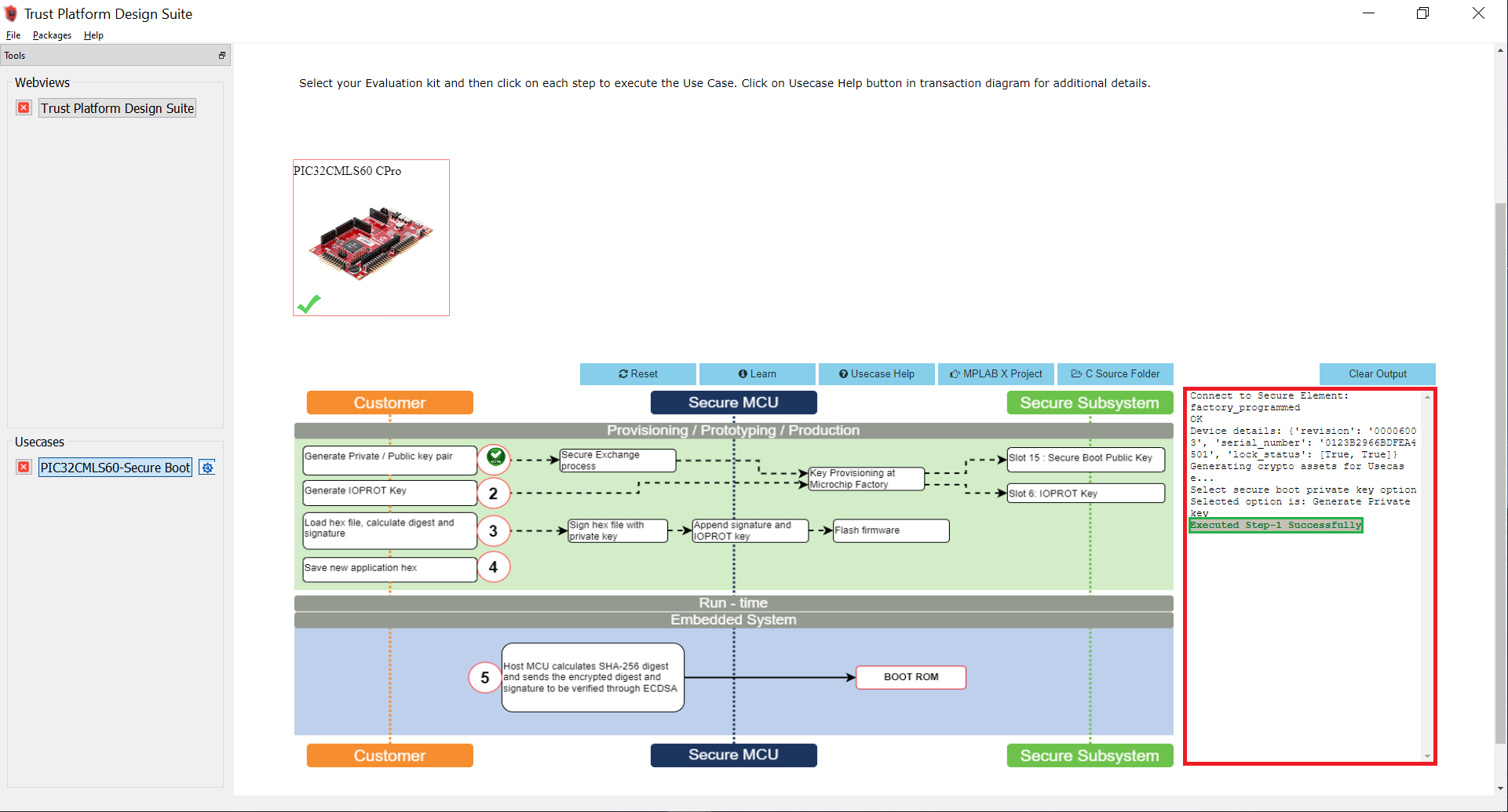
- Select Option 2 to Generate the IOPROT Key.
- The communication between the PIC32CM LS60 microcontroller and the ATECC608B is encrypted using an I/O Protection Key (IOPROTKEY). This unique key is initially provisioned in both the ATECC608B Slot 6 and the microcontroller BOCOR NVM Configuration Row (IOPROTKEY).
-
After successful execution of Option 2, a green tick mark appears in the Option 2 as shown below and check the log window for message “Executed Step-2 Successfully”.
-
Copy the pic32cm_ls60_cpro_Secure.X.production.hex file from
reference_apps/apps/pic32cm_ls60_curiosity_pro/pic32cm_ls60_cpro_secure_boot/hex/secure_bootloader/pic32cm_ls60_cpro_Secure.X.production.hexto<user_path>/.trustplatform/pic32cmls60_secure_bootto load hex file, calculate digest, and signature. -
Select Option 3 to load the Secure Bootloader hex file from the TPDS trustplatform folder i.e.,
<user_path>/.trustplatform/pic32cmls60_secure_bootto calculate the digest and signature. In this step, the digest and signature will be generated for the loaded Secure Bootloader hex file.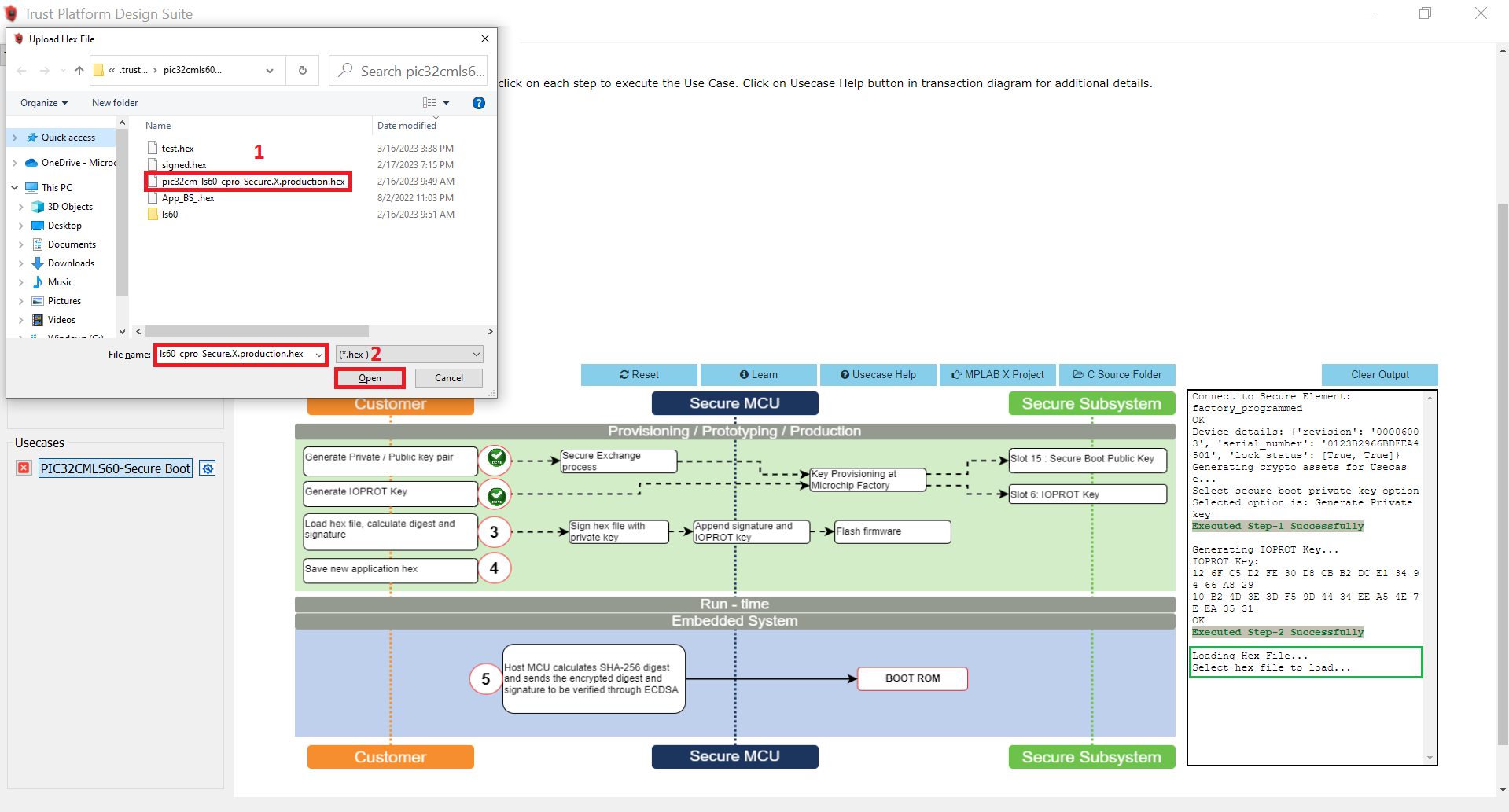
-
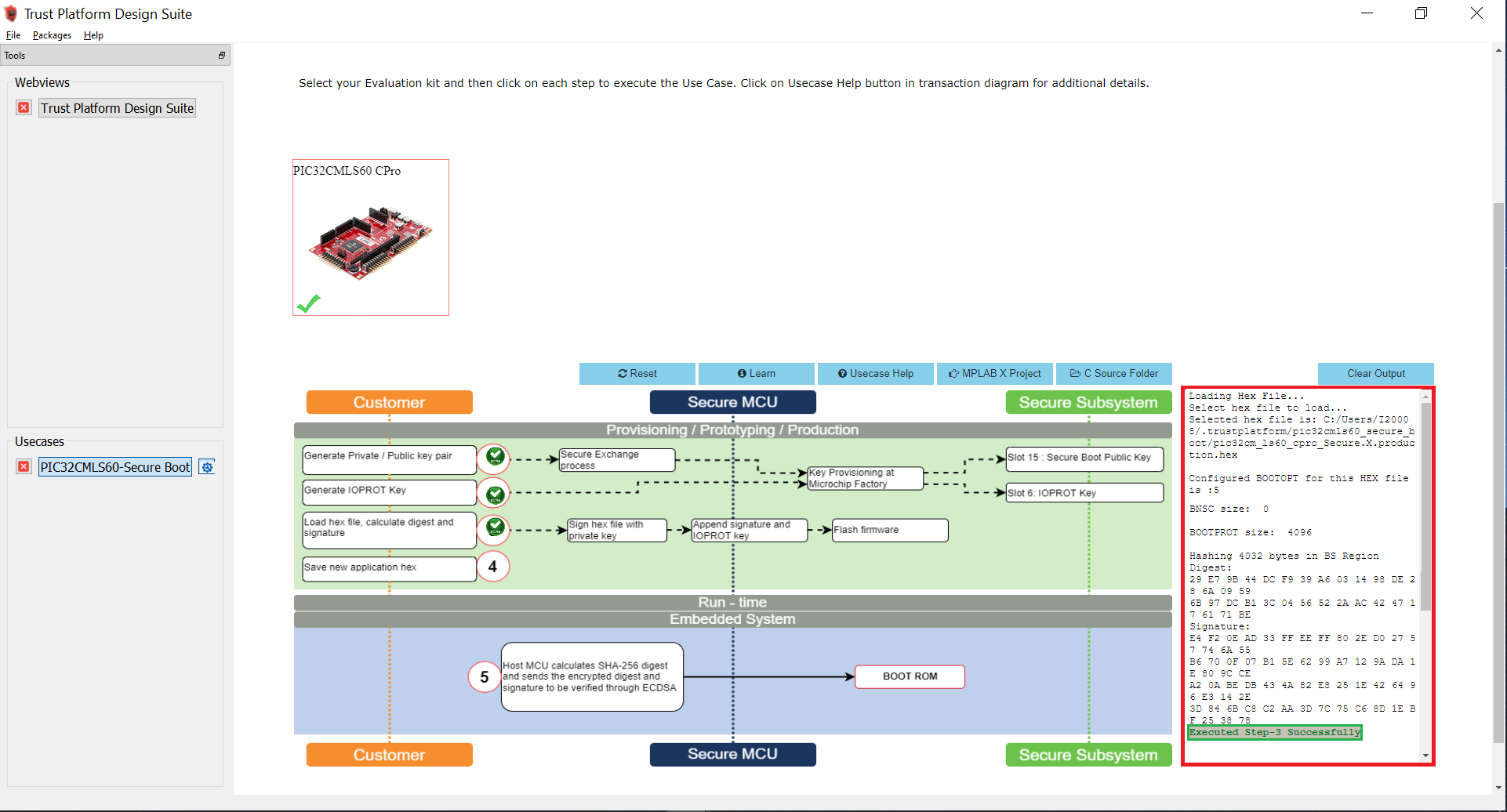
After successful execution of Option 3, a green tick mark appears in the Option 3 as shown below and check the log window for message “Executed Step-3 Successfully”.
-
Select Option 4 to save the new application hex. i.e, the TPDS generates a new hex file with the name signed.hex which has the digest and the Elliptic Curve Digital Signature Algorithm (ECDSA) signature stored at the end of the BOOT region Secure Bootloader hex file.
-
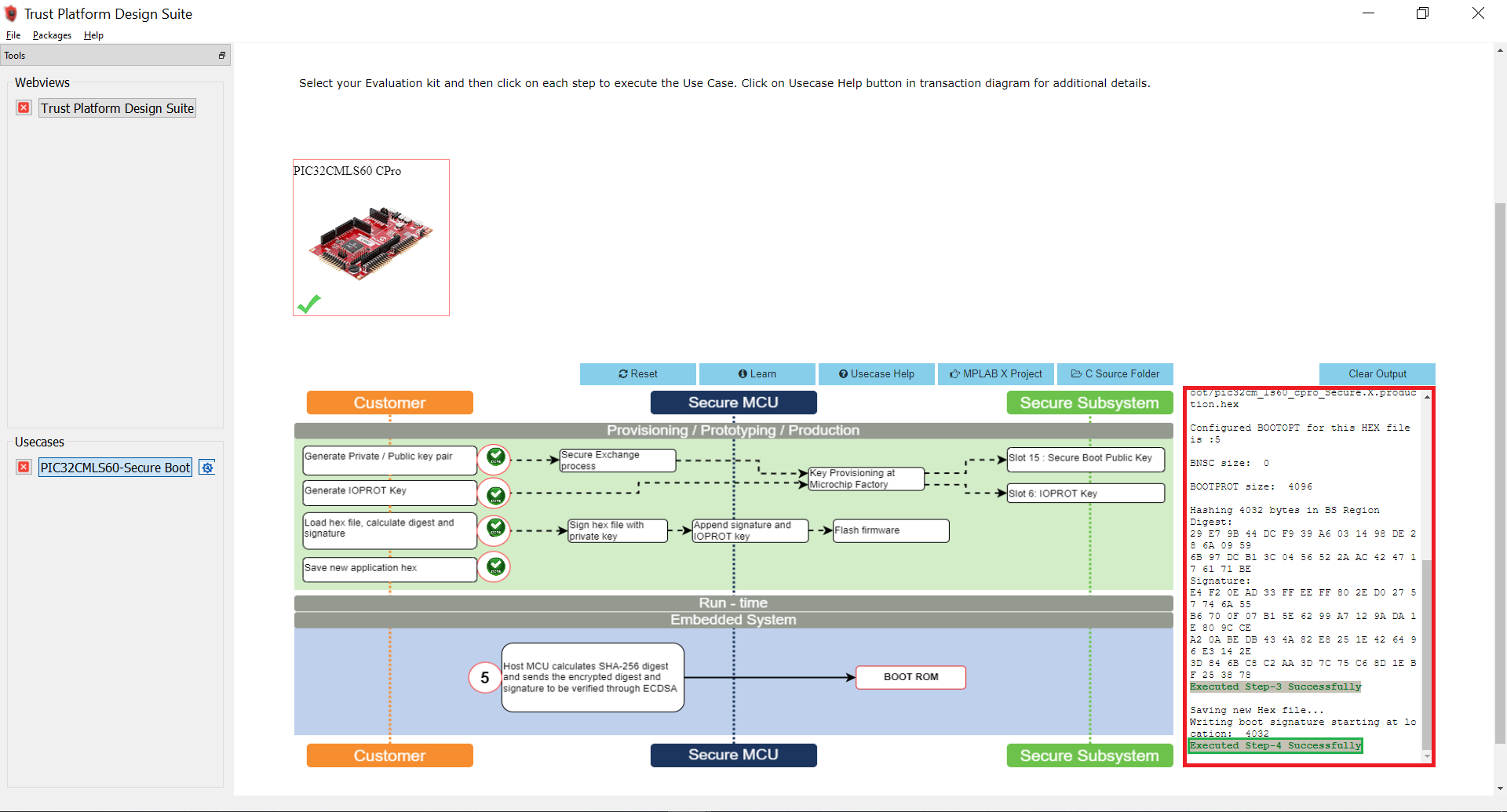
After successful execution of Option 4, a green tick mark appears in the Option 4 as shown below and check the log window for message “Executed Step-4 Successfully”.
-
Select Option 5 to program the signed.hex on to PIC32CM LS60 Curiosity Pro Evaluation Kit. In this step, the Host MCU calculates the SHA-256 digest and sends the encrypted digest and signatures to be verified through ECDSA. Then Secure Boot execution will authenticate the application code.
-
After successful execution of Option 5, a green tick mark appears in the Option 5 as shown below and check the log window for message “Executed Step-5 Successfully”.
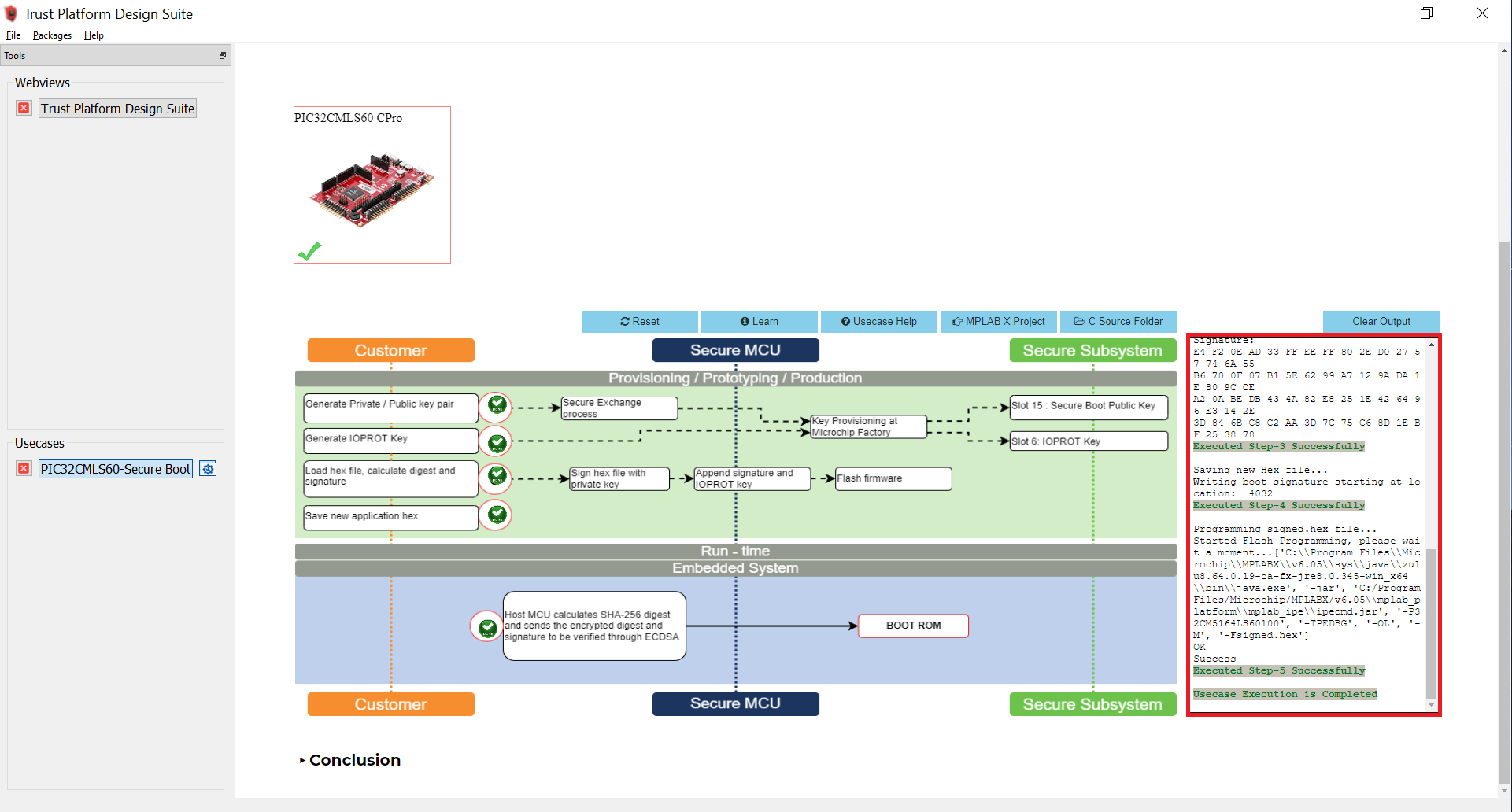
-
This completes the usecase execution. i.e., the provisioning flow of PIC32CM LS60 MCU.
- Reset or power cycle the device.
- Open the TPDS application and select the TrustFlex usecase, i.e., Secure Boot-PIC32CMLS60.
- The successful running of the Secure bootloader is indicated by turning the green LED (LED0) ON.
- A green LED (LED0) on the PIC32CM LS60 Curiosity Pro Evaluation Kit turns ON when the Secure Bootloader is running.
- Open MPLAB X IDE and you can check the Configuration Bits by going to Window->Target Memory Views->Configuration Bits in the MPLAB X IDE
- The Secure Bootloader fuse configuration bits are stored in the secure_bootloader_with_tpds.c file.
- Here, you can see that the BOOTROM_BOOTOPT value is set to 0x5, which enables the secure boot.
- Also check the BOOTKEY which is set by the user and IOPROTKEY which is stored by the TPDS.
- Receive the application image over UART from a PC by running a python script. The successful receiving of the application is indicated by toggling the red LED.
- Open the Virtual Debug COM port and set the baud rate to 115200.
- Connect the Type-A male to Mini-B USB cable to Mini-B USB-UART Cick onboard to receive the application firmware from the Host-PC.
- Go to the Secure Bootloader Scripts path, and open Command prompt to run the bootloader host script btl_host.py and device fuse configuration bits generation script btl_dev_cfg_gen.py.
- btl_host.py - Sends the Application’s Unified (Secure and NonSecure) binary from Host-PC to Target device over UART.
<reference_apps>/apps/pic32cm_ls60_curiosity_pro/pic32cm_ls60_cpro_secure_boot/scriptsand execute the following command. Change the COM port number based on its enumeration in the Host-PC. - btl_dev_cfg_gen.py - Generates the device fuse configuration bits.
-
To show help menu for the script enter
btl_host.py --helpin the command prompt.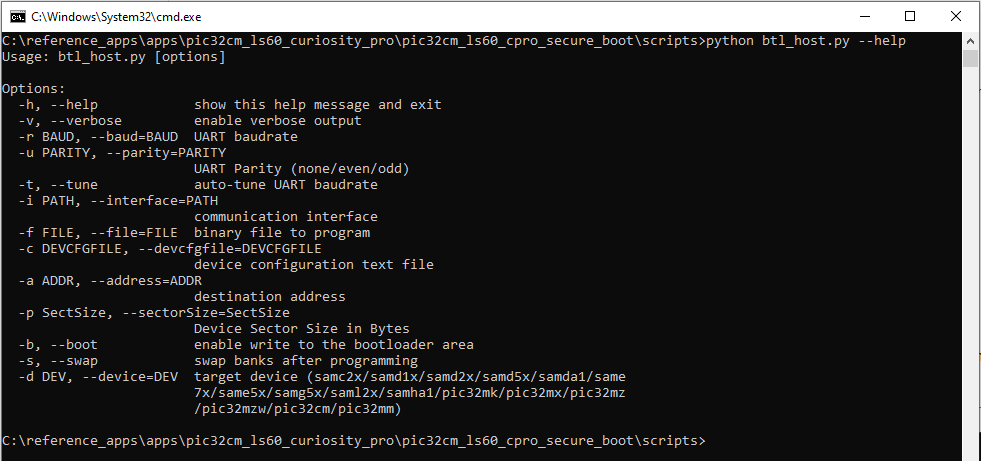
- btl_host.py - Sends the Application’s Unified (Secure and NonSecure) binary from Host-PC to Target device over UART.
-
The following command sends the Application’s Unified binary from Host-PC to the PIC32CM LS60 Curiosity Pro Evaluation Kit and updates the User row fuse configurations bits. See the following output on the command prompt.
-
python btl_host.py -v -u even -i COM27 -d PIC32CM -a 0x1000 -f ../hex/test_app/pic32cm_ls60_cpro_NonSecure.X.production.unified.bin -c application_user_configurations_out.txt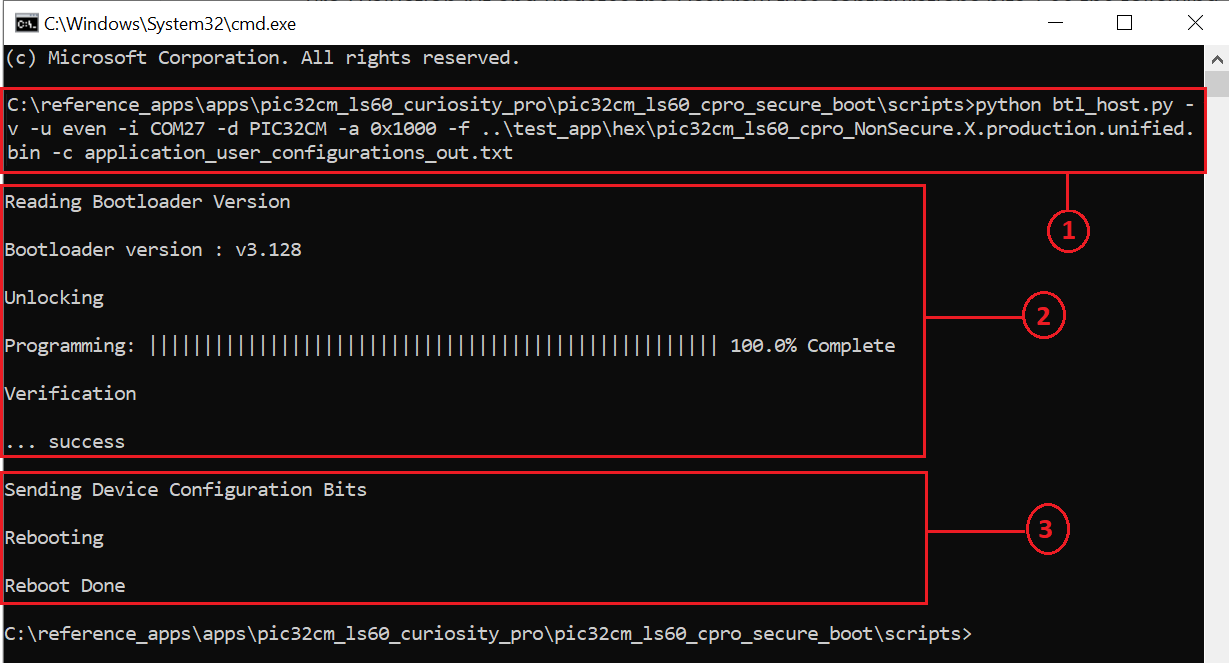
-
Observe the LED1 (Red-LED) blinking while receiving the application.
-
- After receiving the application’s unified binary and update of device configuration bits, remove the Mini-USB from the USB-UART Click board and reset the device.
-
Red LED1 starts toggling indicating secure and successful application booting.
-
Now the LED1 (Red-LED) toggles and prints a message in the Virtual COM as shown below, indicating the application is loaded from Secure bootloader.
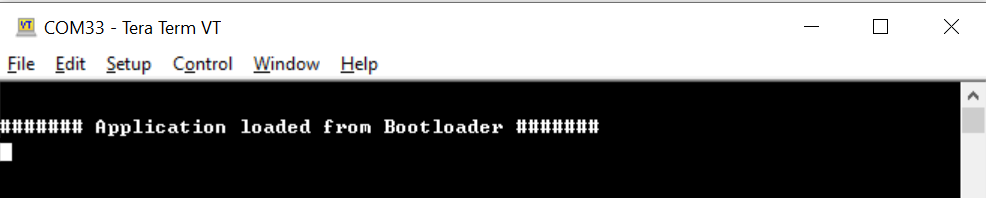
-
Press and Hold the Switch SW0 key to trigger the Secure Bootloader to program the application once again or with the new application.
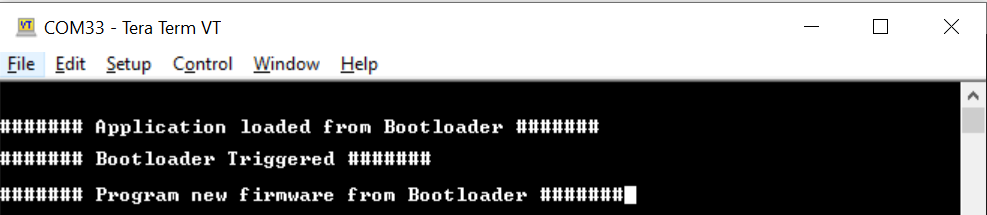
-
Notice that the green LED0 turns ON when the Secure Bootloader is triggered.
- Now open MPLAB X IDE and to check the Device Fuse Configuration Bits after programming the application. Go to Window->Target Memory Views->Configuration Bits in the MPLAB X IDE. The configuration bits are saved in the secure_bootloader_with_tpds_and_application.c file.
- In this file, notice only User Row configurations (i.e., USER WORD) are updated based on the application’s configuration, whereas the Boot Configuration Row (i.e., BOCOR WORD) are not modified.
- You can check the diff of the secure_bootloader_with_tpds.c and secure_bootloader_with_tpds_and_application.c present in the scripts folder to see which user configuration bitfields are updated by the Bootloader script based on the application’s project configuration.
-
Step-2: Impersonating Bootloader
- Open and Build the Secure Bootloader project in the MPLAB X IDE, i.e.,
reference_apps/apps/pic32cm_ls60_curiosity_pro/pic32cm_ls60_cpro_secure_boot/firmware/secure_bootloader/Secure/firmware/pic32cm_ls60_cpro_Secure.X - Program the hex file using MPLAB X IDE.
- Since the Secure Bootloader image does not have the signature appended at the end of the Bootloader image when flashing using the MPLAB X IDE, the ATECC608 B-based authentication and integrity checks fails.
- The Secure Bootloader application fails to Boot. LEDs will go to the OFF state.
Step-3: Restoring the Secure Bootloader and Validation
- Perform Hardware Setup steps mentioned above to restore the Secure Bootloader.
- Generate the Secure Bootloader .hex file in MPLAB X IDE as mentioned in the Step 1.1.
- Use the Private/Public key used in Step 1.2 in TPDS and create the signed .hex file.
- Follow the Step 1.3 to program the signed.hex file using the TPDS. Then press the Reset button and observe that the green LED0 is turned ON. This indicates the successful running of the Secure Bootloader.
- Follow the Step 1.4 to receive the application image over UART from a PC by running a python script. The successful receiving of the application is indicated by toggling the red LED.
- Since the Secure Bootloader is restored and the Secure Bootloader and application work as expected. Red LED1 starts toggling indicating secure and successful application booting.
Note:
- Modifying the security configurations by (re)-programming the different NVM Configuration rows (using the NVMCTRL peripheral) is possible but the changes done on these NVM Configuration rows will always be applied only after a new reset sequence happens (through a new Boot ROM execution).
- The Security Configuration Lock bit i.e., SECCFGLOCK is set to 1 by default. This means, after exiting the Boot ROM:
- The security configurations are locked so that no code (even secure) can change them before next reset sequence.
- The only way to update the security configurations is to (re)-program the NVM Configuration rows then reset the device.
- For more information check the PIC32CM LS00/LS60 Specific Security Features section of PIC32CM LE00/LS00/LS60 Family Data Sheet.
Comments:
- Getting Started with the PIC32CM LE00/LS60/LS60 Curiosity Pro Board
- Trust Platform Design Suite v2
- PIC32CM LS00/LS60 Security Reference Guide
- Dual Developer Application Development Use Case with TrustZone on SAM L11 Using MPLAB Harmony v3
- Note: Though this technical brief is on SAM L11 MCUs, the TrustZone concepts it describes also applies to PIC32CM MC LS60 MCUs.
- This application demo builds and works out of the box by following the instructions above in “Running the Demo” section. If you need to enhance/customize this application demo, you need to use the MPLAB Harmony v3 Software framework. Refer links below to setup and build your applications using MPLAB Harmony.
- How to Setup MPLAB Harmony v3 Software Development Framework
- How to Build an Application by Adding a New PLIB, Driver, or Middleware to an Existing MPLAB Harmony v3 Project
- MPLAB Harmony v3 is also configurable through MPLAB Code Configurator (MCC). Refer to the below links for specific instructions to use MPLAB Harmony v3 with MCC.
Revision:
- v1.6.0 - Released demo application