1.24 TCP/IP WolfSSL TCP Client
This configuration demonstrates creating an Internet client that uses the MPLAB Harmony TCP API to create a TCP/IP connection to a Web server. The connection can either be clear text, or it can use TLS to encrypt the connection with wolfSSL. The demonstration uses IPv4. (But it can use either IPv4 or IPv6)
This demonstration uses the NET_PRES layer for encrypted communication through an external service provider for TLS support.
TCP/IP WolfSSL TCP Client MCC Configuration
The following Project Graph diagram shows the Harmony components included in the WolfSSL TCP Client application demonstration.
MCC is launched by selecting Tools > Embedded > MPLAB® Code Configurator from the MPLAB X IDE and after opening the project, TCP/IP demo project is ready to be configured and regenerated.
TCP/IP Root Layer Project Graph
The root layer project shows that UART2 peripheral is selected to do read and write operation for TCP/IP commands.
This is the basic configuration with SYS_CONSOLE, SYS_DEBUG and SYS_COMMAND modules. These modules are required for TCP/IP command execution.
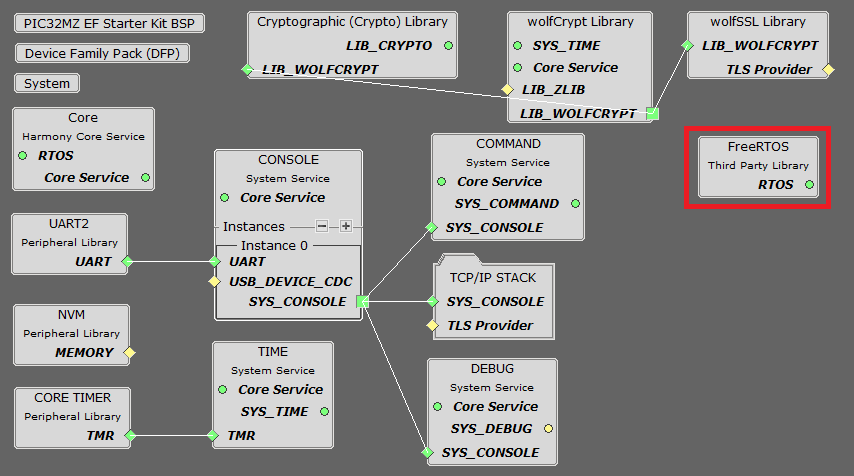
NOTE - The above diagram contains FreeRTOS component and that is required for RTOS application. For bare-metal(non-RTOS) FreeRTOS component shouldn't be selected.
TCP sockets calculate the ISN using the wolfSSL crypto library.
NOTE - The Hardware cryptography is enabled in the wolfCrypt Library's configuration in MCC.
TCP/IP Configuration
PIC32MZ EF Starter Kit
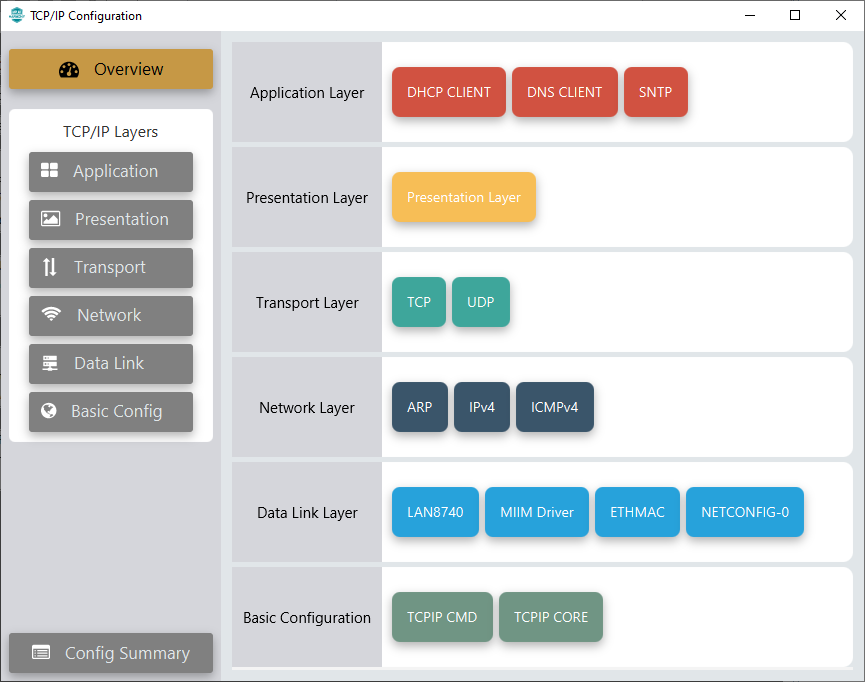
TCP/IP Required Application
TCP/IP demo use these application module components for this demo.
DHCP Client module to discover the IPv4 address from the nearest DHCP Server.
DNS Client provides DNS resolution capabilities to the stack.
SNTP Simple Network Time Protocol updates its internal time periodically using a pool of public global time servers.
TCP/IP Data Link Layer
Internal ethernet driver(ethmac) is enabled with the external LAN8740 PHY driver library for the starter kit. The MIIM Driver supports asynchronous read/write and scan operations for accessing the external PHY registers and notification when MIIM operations have completed.
TCP/IP WolfSSL TCP Client Hardware Configuration
This section describes the hardware configuration for PIC32MZ EF Starter Kit and one can be used for the respective application demonstration.
This section describes the PIC32MZ EF Starter Kit default hardware configuration which uses the on-board debugger and programmer for this application demonstration.
Refer to the PIC32MZ EF Starter Kit User Guide for the programming/debugging options supported & setting up the hardware.
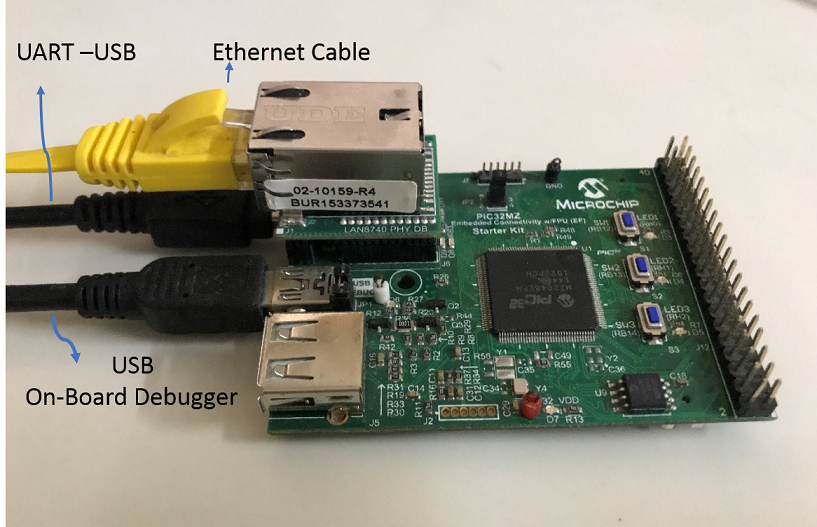
Connect the mini USB cable from the computer to the USB DEBUG connector on the PIC32MZ EF Starter Kit
Connect the mini USB cable from the computer to the USB-UART connector on the PIC32MZ EF Starter Kit
Establish a connection between the router/switch with the PIC32MZ EF Starter Kit through the RJ45 connector on PHY daughter board
TCP/IP WolfSSL TCP Client Running Application
This table list the name and location of the MPLAB X IDE project folder for the demonstration.
| Project Name | Target Device | Target Development Board | Description |
|---|---|---|---|
| pic32mz_ef_sk.X | PIC32MZ2048EFM144 | PIC32MZ EF Starter Kit | Demonstrates the WolfSSL TCP Client on development board with PIC32MZ2048EFM144 device and LAN8740 PHY daughter board. This implementation is based on bare-metal(non-RTOS). |
| pic32mz_ef_sk_freertos.X | PIC32MZ2048EFM144 | PIC32MZ EF Starter Kit | Demonstrates the WolfSSL TCP Client on development board with PIC32MZ2048EFM144 device and LAN8740 PHY daughter board. This implementation is based on FreeRTOS. |
Running Demonstration Steps
Build and download the demonstration project on the target board.
If the board has a UART connection:
A virtual COM port will be detected on the computer, when the USB cable is connected to USB-UART connector.
Open a standard terminal application on the computer (like Hyper-terminal or Tera Term) and configure the virtual COM port.
Set the serial baud rate to 115200 baud in the terminal application.
See that the initialization prints on the serial port terminal.
When the DHCP client is enabled in the demonstration, wait for the DHCP server to assign an IP address for the development board. This will be printed on the serial port terminal.
Alternatively: Use the Announce service or ping to get the IP address of the board.
Run tcpip_discoverer.jar to discover the IPv4 and IPv6 address for the board.
Execution :
As soon as a valid IP address is assigned through the DHCP to the demonstration, it is ready to accept console commands.
There are some commands available in the demonstration from the serial port:
openurl < url > - The < url > argument must be a fully formed URL; for instance, http://www.microchip.com/
ipmode < mode > - The < mode > argument selects the IP version. 0 - Any IP version, 4 - IPv4 only, 6 - IPv6 only
stats - Output the statistics of the previous openurl run. Statistics such as how long each phase of the connection took, and how many bytes were transferred.
unixtime - should be used to test that the SNTP running on board has access to a NTP server.This is needed for the certificate validation (otherwise it will probably not work).
After the successful board bring up, the console output becomes
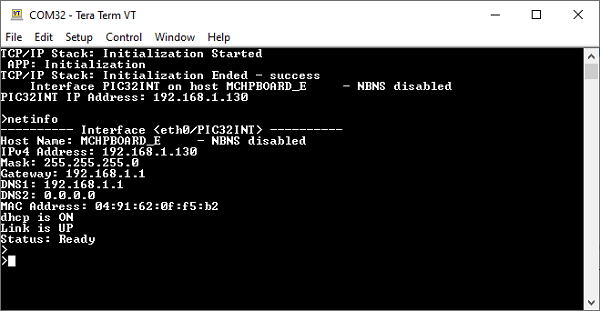
TCP Client Test
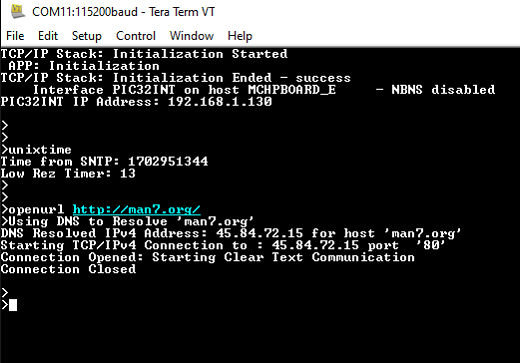
a. Clear text connection (Port 80):
Enter following command in console: openurl < url >. For example, openurl http://www.microchip.com/ or anyother url , the connection established here is clear text.
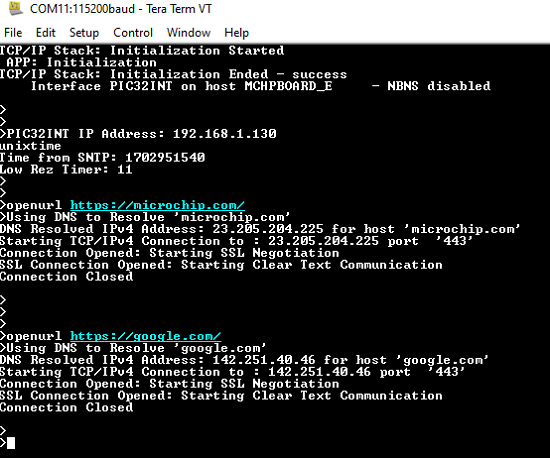
By entering the command unixtime, the response is obtained as shown below.
The expected output -
b. Encrypted connection (Port 443):
Enter following command in console: openurl < url >. For example, openurl https://www.microchip.com/ or https://www.google.com/ , the connection established here is encrypted connection with wolfSSL.
By entering the command unixtime, the response is obtained as shown below.
The expected output -